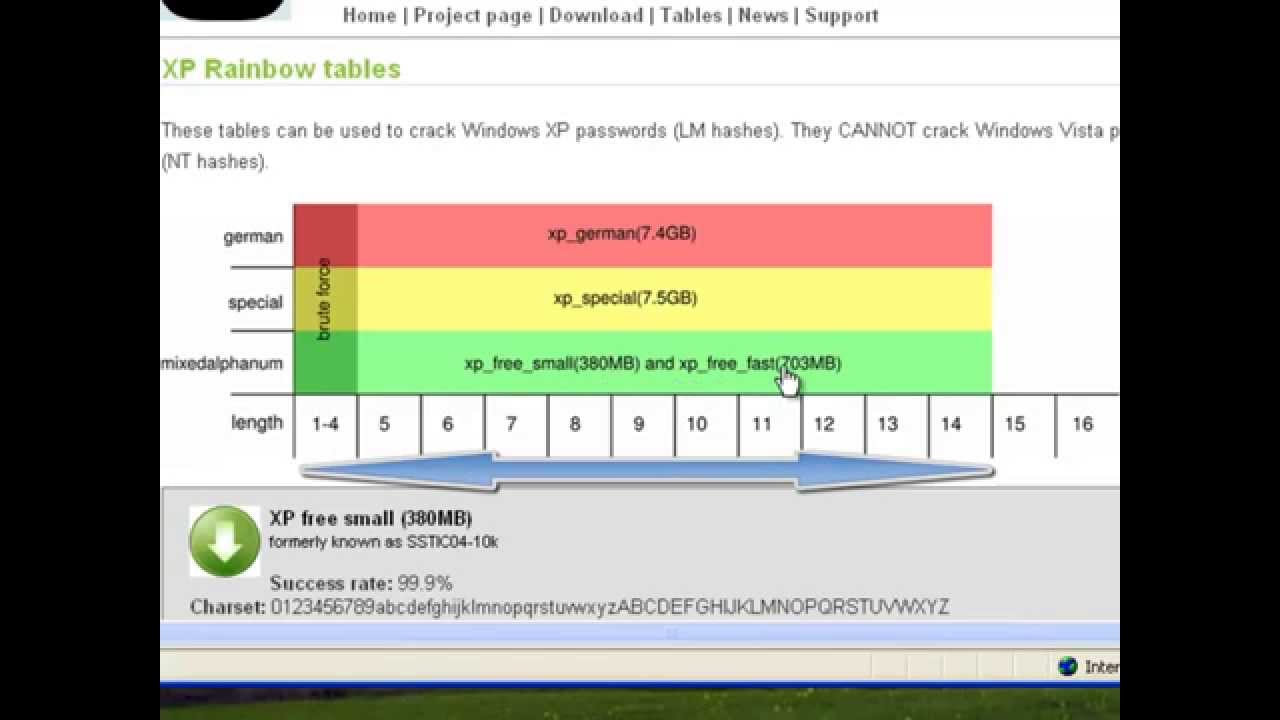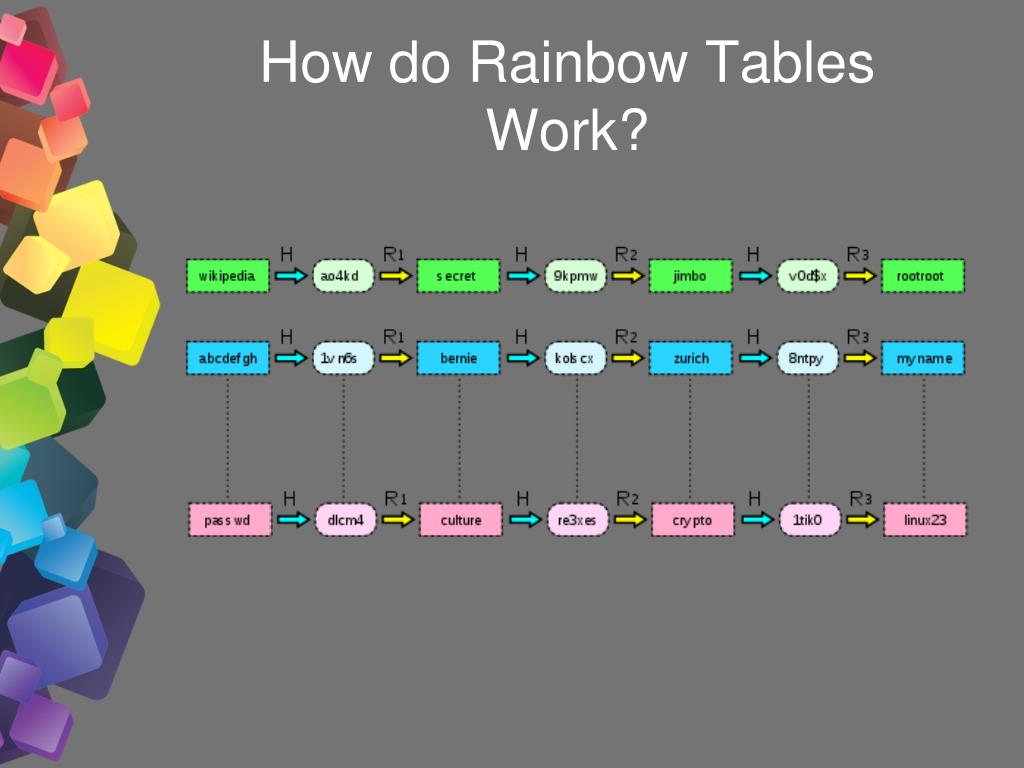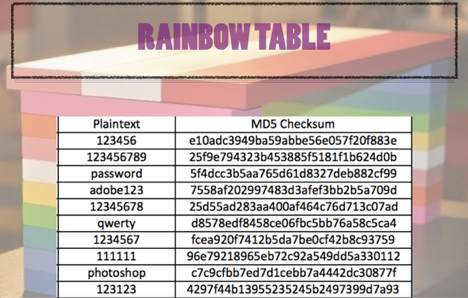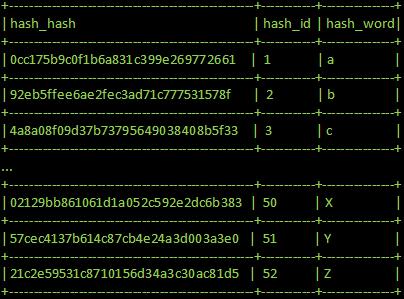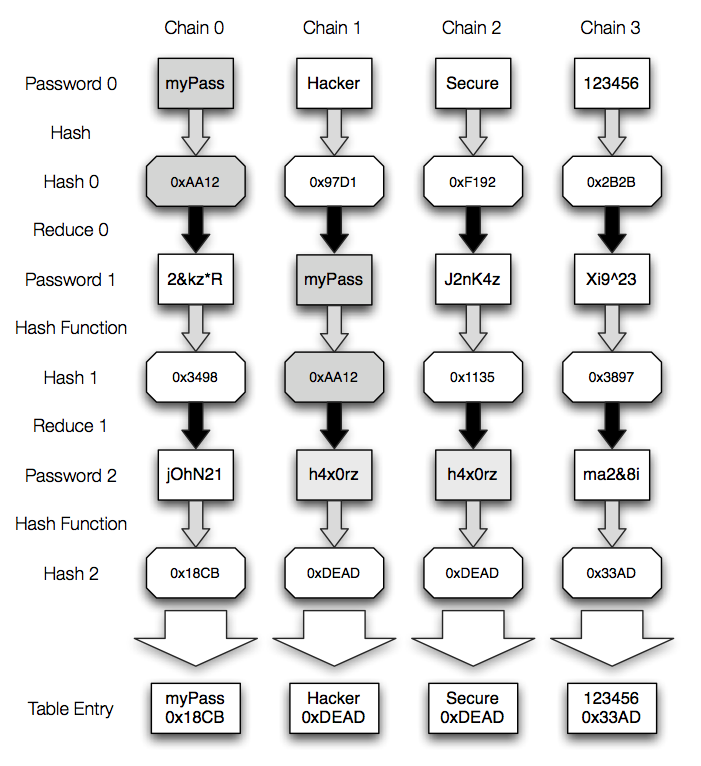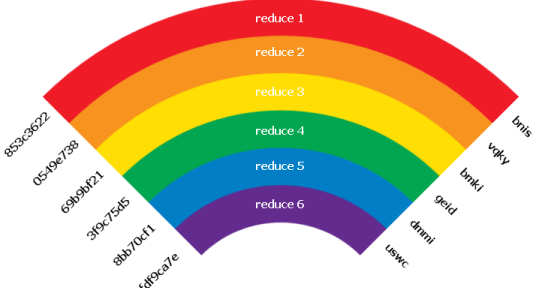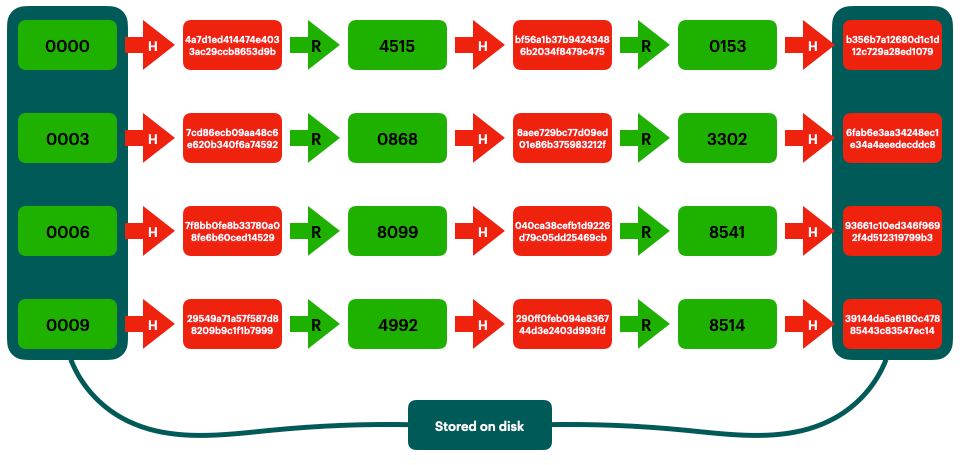
Rainbow Tables (probably) aren't what you think — Part 1: Precomputed Hash Chains | by Ryan Sheasby | Medium
Data Table Having Rainbow Colored Columns | PowerPoint Slide Images | PPT Design Templates | Presentation Visual Aids

Whiz Security - Rainbow Table Attack A rainbow table attack is a type of hacking in which the attackers tries to use a rainbow hash table to crack the passwords stored in

Prof B Buchanan OBE on Twitter: "Be worried about the power of the Cloud to crack hashed passwords ... the threat is not rainbow tables anymore, but Hashcat rules. You say that