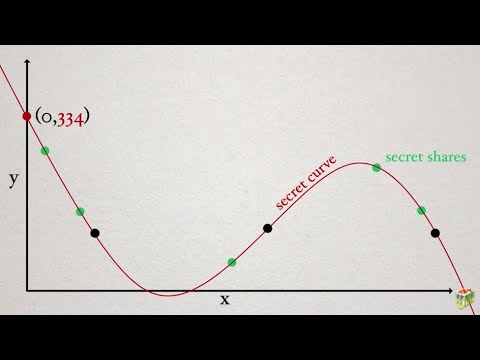
DIMACS Workshop on Coding Theoretic Methods for Network Security 9: :15 AM, April 1 st, 2015 Jason Resch Cleversafe Research Based on “How to Maintain. - ppt download

SETUP in secret sharing schemes using random values - Olimid - 2016 - Security and Communication Networks - Wiley Online Library

4 ways to share secret messages with your friends | Explore | Awesome Activities & Fun Facts | CBC Kids

Figure 3 from A Dual Threshold Secret Sharing Scheme among Weighted Participants of Special Right | Semantic Scholar








![PDF] Application of Biometric Key in Practical Secret Sharing for DNSsec | Semantic Scholar PDF] Application of Biometric Key in Practical Secret Sharing for DNSsec | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/9d617a3c9d82c2432d96075f798331f95055acdf/2-Figure1-1.png)